Eliminate Attack Surface in Open Banking Exchange
Malicious actors can gain access to customer data, such as passwords, sensitive information stored in the bank's systems or unsecured APIs. These unauthorized accesses can lead to financial loss and identity theft. Banks must implement secure technologies, such as encryption and robust access controls to protect customers from these types of threats.
Federated workflows meet growing modularization demand
Service Modularization and Fast Deployment
Bank-FinTech partnerships can play a critical role in delivering value to consumers. Leverage 3rd party FinTech to develop and deploy data, algorithm and the model IP that can plug into the banking or lending system to roll out the service quickly.
Developer-Friendly Runtime Security Insertion
Safelet and SafeStream are designed for DevOps to get started with 3rd party integration and run models securely, all within secure containers.
Secure Integrations and Workflows
SafeLiShare APIs are used as "vaults” to integrate with third-party services, access account data, run workflows without storing any sensitive data.
Fast Response to BSA, GLBA, GDPR & ISO27001 Compliance
Financial institutions are required to protect customer data and honestly disclose all data-sharing practices with customers. SafeLiShare provides tamper-proofed immutable audit logs with app and data “right of access”.

“We partnered with SafeLiShare to fulfill the promise of privacy preservation in banking high-trust data sharing and collaboration. The Secure Data platform has played the key roles for our open banking collaborations”
Addie Lui, Director of Information
Security Aloha Pacific FCU
Eliminate 3rd party unauthorized access and Digital Fraud
- Privacy by design with SafeLiShare’s Secure Enclaves
- Variability, accuracy, and control across the entire partner ecosystem.
- Make access controls, privacy, and governance easy for all parties
- Eliminate OWASP Top 10 API Security
Right Decision can be Taken
- Fast to value market data’s short shelf life without labor intensive de-identification process
- Enable intelligence-led risk decisions
- Preserve privacy in algorithmic trading, volatility forecasting and signal monitoring
Remote attestation of data accuracy, lineage and compliance
- Tamper-proof data access audit on share data and apps with all parties access compliance
- Prevent illegal use or unauthorized application access
People also ask
How does confidential computing improve the security of financial data?
What are some common regulations that fintech companies must follow?
Does SafeLiShare provide capabilities like tokenization and data masking helps to secure financial PII? Why not?
Additional materials
February 21, 2024
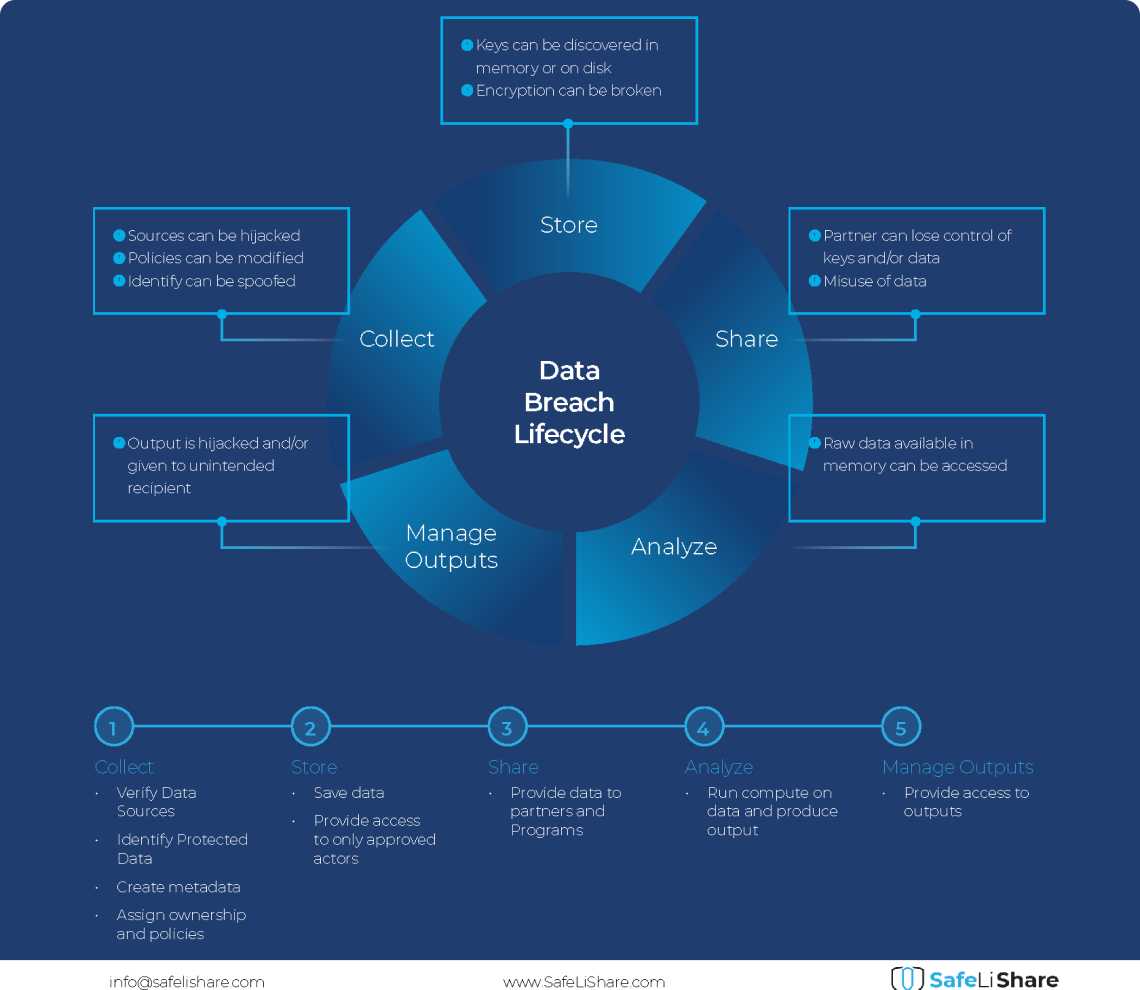
Cloud Data Breach Lifecycle Explained
During the data life cycle, sensitive information may be exposed to vulnerabilities in transfer, storage, and processing activities.

February 21, 2024
Bring Compute to Data
Predicting cloud data egress costs can be a daunting task, often leading to unexpected expenses post-collaboration and inference.

February 21, 2024
Zero Trust and LLM: Better Together
Cloud analytics inference and Zero Trust security principles are synergistic components that significantly enhance data-driven decision-making and cybersecurity resilience.
Experience secure collaborative data sharing today.
Maximize accessibility and monetization of sensitive, regulated, or confidential data without compromise.