Build AI without Sacrificing Data Privacy
SafeLiShare’s data security platform unifies encryption strategies for organizations with hybrid and multi-cloud infrastructures, ensuring data is secure regardless of its location - in use, in motion, or at rest.
- Have concerns about continuous compliance when sharing data with AI / ML programs or cloud services?
- Are you sharing data with other departments across country borders without violating data residency requirements?
- Have concerns sharing user private data with partners for selective use?
By 2025, 60% of large organizations will use one or more privacy-enhancing computation techniques in analytics, business intelligence or cloud computing - Gartner
Overcome Data Sharing Barriers with Hardened Secure Enclaves
Defend Your Business Against the Growing Risk of Insider Attack and Data Theft
Cloud adoption for highly-regulated businesses
Demand isolation and privacy guarantees with hardware-based cryptographic technologies
Multi-party data confidentiality and privacy controls
Results of the processing must be verifiable so that they can be trusted and only provided to authorized parties
Global data residency restrictions and 3rd party access
Verifiable audit logs and PII compliance report on sharing data with 3rd party outside of their borders
Plug-and-Play Runtime Confidential Computing
Provides complete protection for all your data and app assets without infrastructure forklift.
Runtime Confidential Computing
Encryption is a powerful tool for protecting the confidentiality and secrecy of data that falls outside your control.
SafeLiShare’s Confidential Computing solution protects applications and data by encapsulating them in secure enclaves that isolate the datasets to prevent unauthorized access.
Strengthen MultiCloud Data Security
Data rapidly proliferates across multicloud and hybrid IT architectures. SafeLiShare delivers powerful security measures across multiple cloud environments with secure enclave technology to provide an added layer of defense - encryption-in-use, access control, data loss prevention and compliance management.
Deploy in Minutes at Scale with Your Cloud Workloads
Provides hardened vault protection for your data and code with minimal impact.
Natively Integrates with CI/CD Workflow
Integrate within a minute via APIs or initiate secure enclave service in one command line, without any disruption to your infrastructure flow.
Plus, enjoy the centralized access control or set custom policies per organization compliance mandate.
Integrated Visibility and Control
With a single pane of glass, data security, auditors and analysts no longer need to toggle various dashboards.
With deep integration, you get unified visibility and control across clouds and SafeLiShare, greatly simplifying federated workflow, audit reporting, secure enclave provisioning and privilege designation etc.
Bring Compute to Data
Using Policy Driven data flows on public clouds to transfer cumulative results enables the ability to run modern applications on third-party infrastructure in a scalable way while protecting intellectual property and privacy.
Privacy, performance, and protection are never compromised as computation scales up or down.
Integrated Data Security Platform
Integrate within minutes, receive GDPR compliant audits and rich insights, and set fine-grained access controls to protect data privacy with encryption in use.
Multi-Party Data Sharing and Security
Precise encryption and key management within secure enclave to ensure asset-based data privacy and prevent unwanted supply chain compromise.
SaaS Data Security
Validation of secure configuration and interconnection of SaaS platforms is essential when allowing access to running software in public clouds.
SOC and Compliance Automation
Proven to automate and supercharge your data security posture management and deliver trust-worthy result for compliance reporting.
Stop Supply Chain Attacks and Insider Theft Today
Protect your organization from the full spectrum of data security and stop unauthorized third-party access to data in use in the public cloud.
Additional materials
February 21, 2024
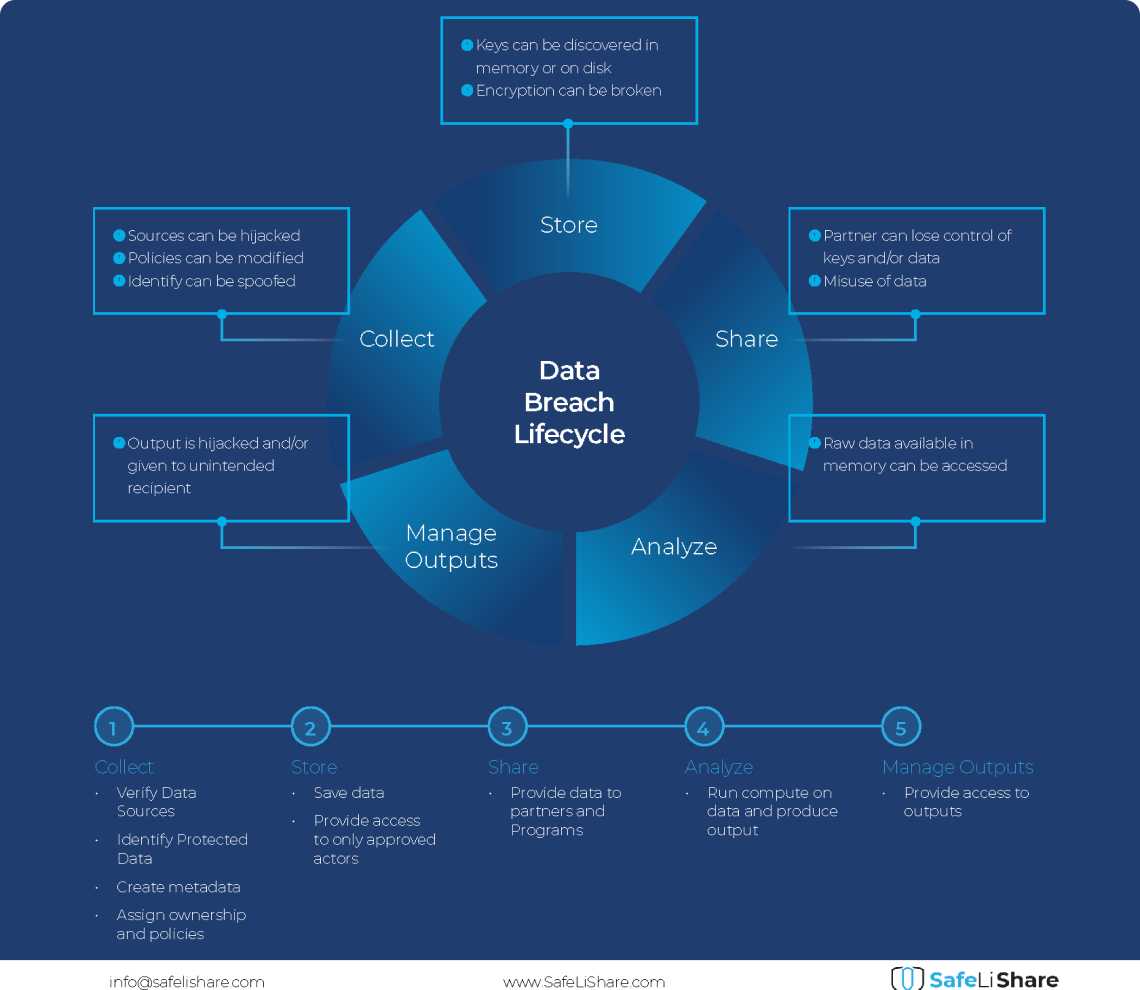
Cloud Data Breach Lifecycle Explained
During the data life cycle, sensitive information may be exposed to vulnerabilities in transfer, storage, and processing activities.

February 21, 2024
Bring Compute to Data
Predicting cloud data egress costs can be a daunting task, often leading to unexpected expenses post-collaboration and inference.

February 21, 2024
Zero Trust and LLM: Better Together
Cloud analytics inference and Zero Trust security principles are synergistic components that significantly enhance data-driven decision-making and cybersecurity resilience.
