Zero Trust Collaboration
Zero Trust Collaboration
Industry 4.0 has brought with it the potential for advanced computing capabilities and data sharing to facilitate the development of smart automation. As new technologies are developed that enable machines and systems to operate at increasingly sophisticated levels, organizations must be able to securely share and analyze data to optimize performance, perform predictive maintenance, and ensure observability of the manufacturing process. Below is a comprehensive overview of the key benefits of data sharing Implementation in Industry 4.0 and how Confidential Computing can provide the hardened security and auditability of who has access to the data, where the data resides, and the protection of the data from competitors.
Improved Data Integration & Collaboration
One of the biggest advantages of data sharing in Industry 4.0 is improved integration among stakeholders across industries and organizations. By creating secure digital connections between stakeholders and allowing automated collaboration on shared projects, data sharing makes it easier for organizations to collect accurate information from multiple sources, which can help improve decision-making processes and achieve better results faster than ever before.
Streamlined Processes & Improved Quality
Another major benefit of effective data sharing in Industry 4.0 is streamlined processes and improved quality control throughout the production process. By having access to real-time updates on production parameters and processing conditions, customers and suppliers can monitor each step more effectively while reducing errors due to manual input processes or incorrect entries. This ultimately leads to producing higher quality products as well as delivering more reliable services efficiently compared to traditional methods utilized in earlier manufacturing revolutions.
Data-Driven Insights & Predictive Analysis
Data sharing allows stakeholders within an industry sector or organization to build powerful insights based on collected customer behavior information or past trends that can be used for analytics to predict, e.g., what customers will purchase next or how markets might react over time under certain conditions. The ability to shed light onto previously unknown trends within the industry provides companies with valuable knowledge which they can use to their advantage when formulating strategies for growth or improvement purposes across functional departments; from finance, sales & marketing all the way up to supply chain management functions amongst others.
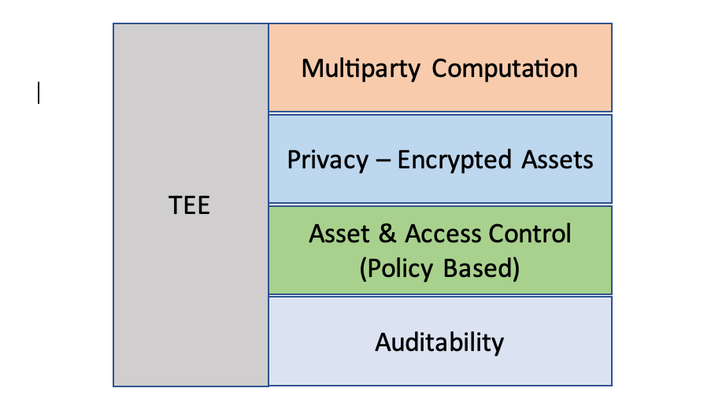
Secure Computation and Data Access with Confidential Computing
The importance of data security has never been more apparent, as businesses continue to rely on technology for every aspect of communication, storage and transactions. A trusted execution environment (TEE) (also known as Confidential Computing) is a group of new technologies that use encryption and public key infrastructure (PKI) to create isolated and protected memory regions where data and workloads can be segmented and processed. These isolated and protected memory regions are sometimes referred to as secure enclaves, using which organizations can securely share data and collaborate on aggregated insights. By leveraging a secure hardware-based “enclave” for computation and data sharing, companies can benefit from confidential computing capabilities embedded in their analytic solutions, creating trust bridges between entities that need to protect their collaboration efforts.
A Trusted Execution Environment (TEE) is a secure area of the main processor in which sensitive processes are isolated with enhanced security measures. It is designed to be resistant to malicious activity such as viruses or malware threats by providing strict authentication systems and cryptographic functions. This allows IT departments to securely execute code even when other applications may be compromised or attacked.
Use TEE Technology to Enhance Data Security
By placing sensitive processes and operations inside the hardware-protected enclave, organizations benefit from stronger protection over important files that could otherwise be targeted by malicious actors. The TEE system can run isolated applications in parallel with other running processes so data remains safe regardless of what happens outside the enclave perimeter. Additionally, any type of communications channel used for transferring data is subject to rigorous encryption protocols ensuring information cannot be intercepted or tampered with during transmission.
Benefits of Utilizing a Trusted Execution Environment for Collaboration Projects
Using a TEE solution provides numerous advantages when it comes to collaborating on large-scale projects involving multiple parties exchanging private information. For example, using a secure enclave based computing platform enables teams with different access requirements to share insights safely without worrying about unauthorized access or interception by third parties – all without compromising performance levels required for completing large-scale tasks quickly. This makes it possible for multiple collaborators (e.g., partners, suppliers) within different industries (e.g., banking, healthcare) to work together when compiling analytics reports without breaking compliance needs tied with handling sensitive data such as personal records or financial documents belonging to the relationship network participants involved in the project at hand.
Conclusion
Trusted execution environment technologies may be used to provide a cost-effective solution for organizations that need privacy assurances to collaborate on processing data that is shared between the collaborating partners. The insights derived from such collaborative efforts may be integrated back into workflows of the collaborating partners
Experience Secure Collaborative Data Sharing Today.
Learn more about how SafeLiShare works
Suggested for you
February 21, 2024
Cloud Data Breach Lifecycle Explained
During the data life cycle, sensitive information may be exposed to vulnerabilities in transfer, storage, and processing activities.

February 21, 2024
Bring Compute to Data
Predicting cloud data egress costs can be a daunting task, often leading to unexpected expenses post-collaboration and inference.

February 21, 2024
Zero Trust and LLM: Better Together
Cloud analytics inference and Zero Trust security principles are synergistic components that significantly enhance data-driven decision-making and cybersecurity resilience.